- | Technology and Innovation Technology and Innovation
- | Data Visualizations Data Visualizations
- |
Federal Cybersecurity Breaches Mount Despite Increased Spending
This week’s charts use data from the Congressional Research Service and the Government Accountability Office to display total federal cybersecurity spending required by the Federal Information Security Management Act of 2002 (FISMA) with the total number of reported information security incidents of federal systems from 2006 to 2013.

In the wake of the high-profile cybersecurity breach at Sony Pictures Entertainment in December, President Obama unveiled reform proposals that would increase the federal government’s ability to direct American cybersecurity practices. These proposals, which include increased federal funding, a cybersecurity summit, and legislative changes to encourage information-sharing among private sector organizations and government bodies, are only the most recent efforts in a long line of government attempts to nationalize and influence private cybersecurity practices. Despite years of increased cybersecurity spending, the federal government already has a poor track record in maintaining good cybersecurity and information-sharing practices for its own information technology (IT) systems.
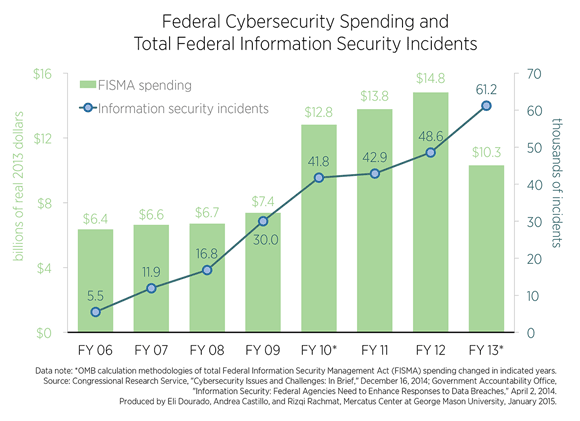
This week’s charts use data from the Congressional Research Serviceand the Government Accountability Office to display total federal cybersecurity spending required by the Federal Information Security Management Act of 2002 (FISMA) with the total number of reported information security incidents of federal systems from 2006 to 2013. The first chart shows that the number of federal cybersecurity failures has increased every year since 2006, even as investments in cybersecurity processes and systems have increased considerably.
FISMA was intended to strengthen federal IT systems by requiring agency leaders to develop and implement information security protections with the guidance of offices such as the National Institute of Standards and Technology (NIST), the Office of Management and Budget (OMB), and the Department of Homeland Security (DHS). In addition to authorizing the sums necessary for agencies to invest in cybersecurity technologies and infrastructure, FISMA compels agencies to proactively assess and reduce systematic risks, actively train personnel to meet and improve information security standards, improve cybersecurity risk reporting and information sharing capabilities, and develop contingency plans to respond to cyber-breaches.
Total FISMA information security spending reported by the OMB from FY 2006 to FY 2013 measured in real 2013 dollars is displayed on the chart in light green bars and measured on the left axis. The chart shows that federal spending on information security investments exhibited moderate growth over much of the period. Both the dramatic increase in FISMA spending from $7.4 billion in FY 2009 to $12.8 billion in FY 2010 and the dramatic decrease in FISMA spending from $14.8 billion in FY 2012 to $10.3 billion in FY 2013 are partially attributable to OMB’s decision to change its FISMA spending calculation methodology in those years. Even with this caveat on inter-year comparisons, the chart shows that the federal government has invested billions of dollars to improve its internal cybersecurity defenses in recent years. Altogether, the OMB reports that the federal government spent $78.8 billion on FISMA cybersecurity investments from FY 2006 to FY 2013.
Increased federal spending on cybersecurity, however, is not reflected in the rate of cyber-breaches of federal systems reported by the GAO. The total number of federal information security incidents reported from 2006 to 2013 is displayed by the blue line on the chart and measured on the right axis. The number of reported federal cybersecurity incidents increased by an astounding 1,012% over the selected years, from 5,503 in 2006 to 61,214 in 2013.
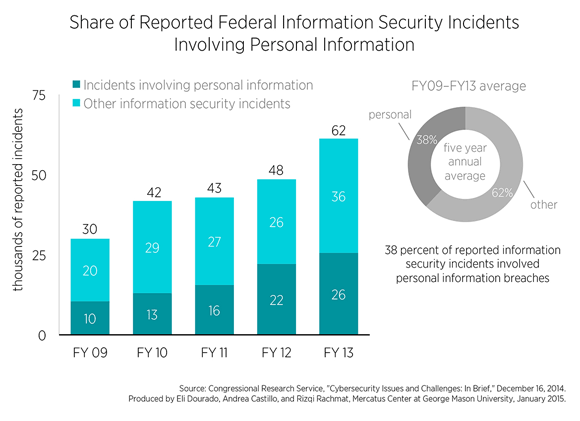
It is troublingly that many of these breaches exposed the personally identifiable information of federal personnel, veterans, and even civilians stored in federal systems to potential access by external groups. The second chart displays the proportion of all reported federal information security incidents that involved the exposure of personally identifiable information from 2009 to 2013. Federal information security failures that expose sensitive details about individuals’ lives—including data such as contact information and even Social Security numbers and financial information—have constituted roughly a third of all cybersecurity failures and is an increasing problem. By 2013, more than 40 percent of all reported cybersecurity failures involved the potential exposure of private data to outside groups.
Increased federal spending on cybersecurity investments do not seem to have stemmed the rate of federal information security failures. Despite first sounding the alarm about poor government information security practices in 1997, the GAO reported in April 2014 that federal agencies systematically fail to meet federal security standards owing to poor implementation of key FISMA practices outlined by the OMB, NIST, and DHS. After more than a decade of billion dollar investments and government-wide information sharing, in 2013 “inspectors general at 21 of the 24 agencies cited information security as a major management challenge for their agency, and 18 agencies reported that information security control deficiencies were either a material weakness or significant deficiency in internal controls over financial reporting.”
The federal government’s own failure to improve internal cybersecurity practices after years of increased spending and information-sharing among agencies calls into question the effectiveness of President Obama’s proposals to extend these policies to the private sector. While cybersecurity vulnerabilities and data breaches remain a considerable problem in the private sector as well as the public sector, policies that failed to protect the federal government’s own information security are unlikely to magically work when applied to private industry. The federal government’s own poor track record of increasing data breaches and exposures of personally identifiable information renders its systems a dubious safe house for the huge amounts of sensitive data affected by the proposed legislation. The federal government should focus on properly securing its own IT systems before trying to exert more control over private systems.

